Traffic Sentinel is configured with a set of packet signatures that describe known vulnerabilities. The following signature is an example of the type of rules that are uses to identify attacks (rules are expressed using Snort® syntax):
alert tcp $HOME_NET any -> any 80\ (\ msg:"WEB-IIS cmd.exe";\ flow: established;\ uricontent:"cmd.exe"; nocase;\ classtype:attempted-user;\ sid:1002; rev:1;\ )
This rule looks for hosts on the home network that are sending web requests containing the pattern "cmd.exe" in the URL. When traffic matching the rule is identified, an event is generated.
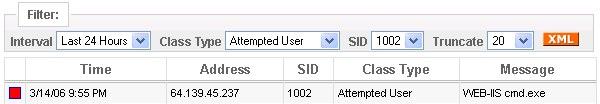
The event log shows identifies host 64.139.45.237 as violating rule number 1002. Clicking on this entry provides additional information about the host.