Policy Violation
Being proactive is an essential part of maintaining a secure network. Setting and enforcing policies that eliminate unnacceptable risks catches problems before networks are compromised. Security policies should address the types of applications and devices that are allowed on the network; eliminating non-essential and non-secure applications and devices reduces the number of possible security threats.
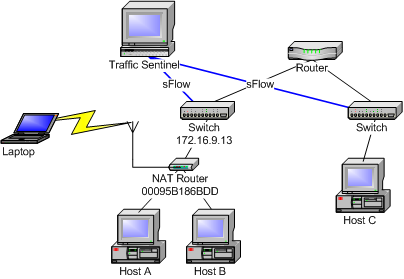
In this example we have a policy that forbids users to attach their own routers to the network. Of particular concern are NAT (Network Address Translation) routers. Typically a NAT router will appear to the network administrator as a single host and will authenticate itself with the network. Any number of unauthorized hosts can then be attached to the NAT router and obtain unrestricted access to the nework. If the NAT router provides wireless (Wi-Fi 802.11) access then it can provide access to the network from a considerable distance, allowing unauthorized access without even entering the building.
Traffic Sentinel's network-wide monitoring capability makes enforcement of this policy straightforward. Enforcement of this policy without network monitoring is extremely difficult, exposing the network to serious security risks.