Intrusion Detection
Traffic Server makes use of sFlow® to provide intrusion detection capabilities that complement existing firewall functions.
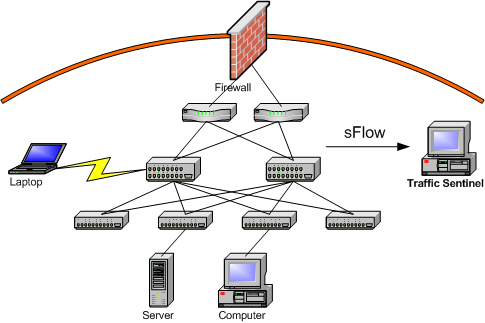
The map shows some of the elements of a typical site network. Traffic from the Internet passes through a firewall before entering the site. Traffic is then routed to distribution switches, providing connectivity to the computers on the site.
Unfortunately, no firewall provides complete security:
- A new attack may compromise hosts before the firewall rules can be updated.
- Laptops may become compromised when offsite and then infect machines behind the firwall when they are connected to the network.
- Wireless access points may allow intruders into the site. Even if authorised wireless access points are secure, a careless user may attach an unsecured access point to the network.
- Multiple infection vectors, including email, web and plugins make it extremely difficult for the firewall to identify all possible threats.
Security problems behind the firewall can be very hard to detect and isolate. Fortunately, the pervasive monitoring capability of Traffic Sentinel provides a cost effective way of applying intrusion detection techniques to the traffic throughout the internal network.
This example shows how the intrusion detection capabilities of Traffic Sentinel can be used to detect an intrusion attempt by a local host.