The following table shows detailed information about the switch interface connecting the unauthorized router to the network:
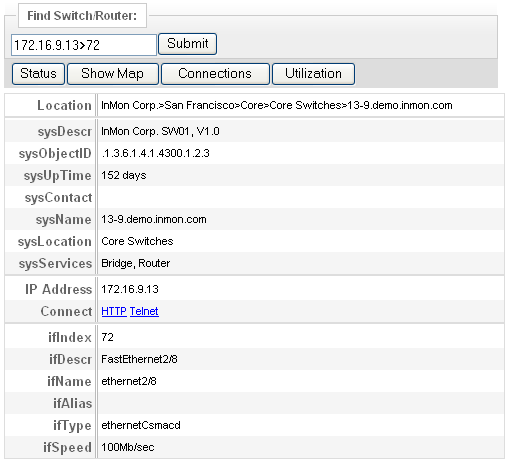
At this point there is enough information to disable this interface, disconnecting the unauthorized router from the network (the Connect links provide access quick access to the command line and web interfaces on the switch). Instead we could choose to gather further information by clicking on the Connections button to see in real-time the current activity on the switch port (for more information on real-time monitoring see the Ensure Quality of Service example).
The next example demonstrates how Traffic Sentinel is used to detect Suspicious Behavior.